CMS Enveloped Data
PDF certificate security is based on the Cryptographic Message Syntax (CMS) according to RFC 5652. CMS describes an encapsulation syntax for various cryptographic features including digital signatures, message authentication and encryption. PDF certificate security makes use of the EnvelopedData functionality provided by CMS; encrypted e-mail works in a similar manner. To optimize storage requirements and performance certificate security is implemented in a hybrid manner: first an encryption key is created randomly and encrypted against each recipient’s certificate. This process then uses public key encryption based on the RSA or Elliptic Curve Cryptography (ECC) algorithms and stores the encrypted versions of the random key in the CMS object. The random key is used to encrypt the actual CMS payload with a symmetric algorithm and store it in the CMS. Modern implementations generally use the AES algorithm for symmetric encryption. See Cryptographic Details for more details on this process and the involved algorithms.
Each recipient uses his private key to decrypt the symmetric key, and then uses the resulting key to decrypt the CMS payload. The combination of encrypted payload and an encrypted content encryption key for each recipient is called a digital envelope.
Since the first encryption step is asymmetric and the random key is kept only temporarily, the creator of an encrypted document cannot decrypt it later unless his own certificate is included in the list of recipients.
There are two reasons for the hybrid approach with asymmetric and symmetric encryption. Firstly, asymmetric encryption is very slow and suited only for small amounts of data. It is therefore applied only to the short symmetric encryption key and not the full payload. Secondly, this approach allows the payload to be encrypted only once with symmetric encryption, while only the short encryption key must be encrypted individually for each recipient. Encrypting the payload for each recipient would significantly increase the output file size.
The EnvelopedData structure in a CMS object contains one or more RecipientInfo structures. Each of these contains information about a recipient’s certificate – usually the certificate issuer (CA) and serial number – and an encrypted key for the recipient.
Recipient confidentiality
The recipient names are not present in the CMS object. However, the name of the certificate issuer as well as the certificate’s serial number can be retrieved from the CMS object without decryption. For certificates retrieved from a Public Key Infrastructure this means that only the name of the CA and the serial number are exposed. Depending on the PKI this information may or may not be sufficient for identifying the recipient. However, for self-signed certificates the certificate holder herself signs the public key. As a result, the names of all recipients with self-signed certificates are visible in plaintext in the CMS object. In some situations exposing recipient information may be undesirable. You can solve this problem by avoiding self-signed certificates, or by using pseudonyms in self-signed certificates.
Number of recipients and CMS size
A document can be encrypted against an arbitrary number of recipient certificates. However, since a uniquely encrypted key is embedded for each additional recipient, the size of the CMS increases with the number of recipients. The file size expansion depends on the length of the recipient’s public key and the amount of information in the certificate. Typically, the output file size increases by ca. 1-2 KB per recipient.
Applying CMS to PDF Documents
A PDF document encrypted with certificate security contains one or more CMS object in the Recipients entry of the Encrypt dictionary. However, PDF doesn’t apply the CMS mechanism directly to the document contents, but adds another layer of encryption which is identical to password security. The CMS payload doesn’t contain any PDF objects, but keying material which is used to derive the encryption key for PDF objects. The symmetric algorithms used for encrypting PDF objects are the same which are used for password security. While certificate security derives the document encryption key from the encrypted keying material in the CMS, password security derives this key from the secret password.
PDF permission restrictions
The same permission restrictions as for password security can be applied to documents protected with certificate security (see Permissions). In addition to the permission restrictions for password security the following setting is possible with certificate security:
- Restrict printing and editing of the document and its security settings (see top of figure): If this restriction is active, the recipient can open and read the document, but certain operations such as printing and modifying the document are governed by other permission restrictions. If this restriction is not active, the recipient has full control over the document and can also change the security settings. This is similar to documents protected with password security where the user knows the master password. For this reason we call this master permission.
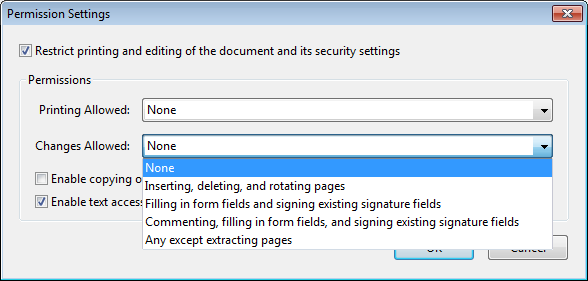
Different users may be assigned different permission restrictions. For example, in an enterprise context a manager may be assigned master permission so that she can edit the document, change the encryption or apply any other change, while her coworkers are only allowed to fill form fields and sign the document. The ability to apply specific permissions to each recipient or group of recipients is an important advantage of certificate security over password security.
The permissions are included in the CMS payload which is encrypted for a particular recipient. For this reason permission restrictions for a specific recipient can only be determined upon decryption for this recipient. It is not possible to query a recipient’s permissions without access to the corresponding digital ID.
Permission handling is a noteworthy difference between certificate security for PDF documents and e-mail. A PDF document can contain multiple CMS objects, where each object may in turn address a group of several recipients. Encrypted keys for recipients with the same permissions are stored in the same CMS object.
