Cryptographic Details
Certificate security involves multiple encryption steps which may use different algorithms and key lengths. For the encryption steps described, see the Figure below.
Step 1: CMS public key encryption and key wrap
Public key encryption is deployed to encrypt a randomly generated content encryption key (CEK), where the details vary between RSA and ECC recipient certificates. Different recipients may use a mixture of RSA and ECC keys as well as different RSA key lengths or ECC curves.
If the recipient’s certificate contains a public key for the RSA algorithm (RFC 5652), this key is used to encrypt the content encryption key. The supported RSA key lengths are not specified in the PDF Reference, but depend on the Acrobat version.
If the recipient’s certificate contains a public ECC key (RFC 5753), the Elliptic Curve Diffie-Hellman (ECDH) key agreement scheme and the public key in the recipient certificate are used to derive yet another temporary key encryption key. A symmetric encryption algorithm called key wrap algorithm is then used to encrypt (wrap) the content encryption key with the key encryption key. Acrobat XI/DC uses AES-128 or AES-256 as key wrap algorithm. The supported ECC curves are not specified in the PDF Reference, but depend on the Acrobat version.
Step 2: CMS content encryption
The content encryption key is used to encrypt the PDF encryption keying material (not the actual key itself) with a symmetric algorithm, resulting in the encrypted CMS payload. With PDF certificate security the CMS »content« doesn’t contain any PDF document data, but instead some keying material from which the final encryption key for PDF objects is derived.
The CMS content encryption algorithm can be selected from a number of algorithms. Acrobat 7-X always use Triple-DES, while Acrobat XI/DC use AES-128. Since payload encryption is required only once regardless of the number of recipients, the choice of algorithm doesn’t depend on the recipient certificates.
Step 3: PDF encryption
The PDF encryption key is applied to PDF objects which results in the data for displaying the document. This step is identical to password security.
The symmetric algorithm and key length for encrypting PDF objects are specified in the PDF reference and correspond to a subset of those used for password security (see table below). The same symmetric algorithm is used to encrypt all objects in the PDF document. Only the algorithm for step 3 can be selected in Acrobat (see figure below). For the strong encryption introduced with Acrobat 7 and Acrobat 9 the PDF encryption algorithm is AES-128 or AES-256, respectively.
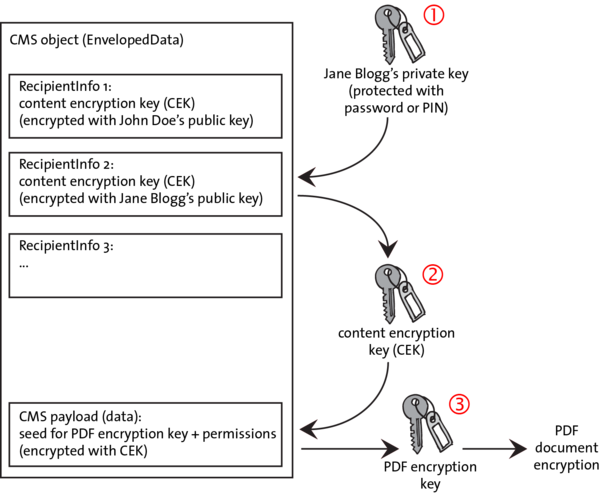
The CMS EnvelopedData structure contains encrypted keys for all recipients with the same permissions. A PDF document contains one or more CMS objects (one for each set of permissions).
Algorithms and key lengths
The table summarizes algorithms and key lengths for various PDF and Acrobat versions. The RC4 and AES-128 algorithms are deprecated in PDF 2.0.
| PDF and CMS encryption algorithms for certificate security and support in Acrobat | |||
| PDF and Acrobat version | Step 1: CMS public key algorithm | Step 2: CMS content encryption | Step 3: PDF encryption |
| PDF 1.4 (Acrobat 5) | Acrobat 6 and above: 2048-bit RSA | Acrobat 6-X: Triple-DES Acrobat XI/DC: 128-bit AES | 128-bit RC4 (deprecated in PDF 2.0) |
| PDF 1.6 (Acrobat 7) | Acrobat 7 and above: up to 4096-bit RSA Acrobat 8 and above: up to 8192-bit RSA1 | Acrobat 7-X: Triple-DES Acrobat XI/DC: 128-bit AES | 128-bit AES (deprecated in PDF 2.0) |
| PDF 1.7ext3 (Acrobat 9) | Acrobat 9 and above: up to 8192-bit RSA2,3 | Acrobat XI/DC: 256-bit AES | 256-bit AES |
1) RSA-8192 keys require Acrobat X or above and are not supported by Acrobat on macOS.
2) When decrypting documents with an ID in the Windows certificate store, Acrobat supports only keys where the length is a multiple of 8 bits.
3) RSA with OAEP padding is not supported in Acrobat DC and below.
4) Acrobat DC 2017.012.20093 Continuous track or above required, see Acrobat Incompatibilities when using ECC Recipient Certificates.
